Take control of your applications and safeguard your data with a comprehensive Application Control Engine buyer’s guide.
By InvestNust
Demystify Application Control Engines! This guide explores features, benefits, considerations & more to help you choose the right ACE for your business.

Understanding the Importance of Application Control Engines (ACE) in Cybersecurity
In today’s digital world, businesses are increasingly dependent on various applications for their operations, from productivity tools to customer relationship management (CRM) software. However, these applications contain sensitive data that must be protected. Firewalls alone are not sufficient to safeguard them, which is where an Application Control Engine (ACE) becomes essential.
What is an Application Control Engine (ACE)?
An Application Control Engine (ACE) is a security tool that scans and regulates application activity across networks or endpoint devices. It acts as a digital gatekeeper, permitting only approved applications to run while blocking unauthorized ones. ACEs help prevent malware infections, data breaches, and unauthorized access to critical systems.
Benefits of an Application Control Engine
Implementing an ACE provides several significant advantages for organizations:
1. Stronger Security
- ACEs reduce the likelihood of malware attacks and data breaches by blocking unauthorized applications, which could be potential threats.
2. Enhanced Compliance
- ACEs help organizations meet industry-specific compliance requirements by limiting access to sensitive data and restricting the use of unauthorized applications.
3. Increased Productivity
- By blocking non-business-related or harmful applications, ACEs ensure that employees stay focused on tasks critical to the business.
4. Reduced Operational Costs
- ACEs simplify the management of IT infrastructure by automating application policy enforcement, thus reducing the need for manual intervention and optimizing resource allocation.
Key Features to Look for in an ACE
When selecting an Application Control Engine, consider the following features to ensure it meets your business needs:
1. Visibility and Control
- Choose an ACE that provides detailed insights into application activity and offers granular control over what is allowed to execute within your network.
2. Threat Detection
- Select an ACE with integrated threat intelligence, capable of identifying malicious applications and preventing potential security breaches.
3. Scalability
- Ensure the ACE can scale as your business grows, accommodating new applications and increased network traffic without compromising performance.
4. Ease of Use
- The ACE should have an intuitive user interface that allows your IT team to easily implement and manage security policies related to application control.
5. Integration
- Opt for an ACE that integrates seamlessly with your existing security infrastructure, such as firewalls, antivirus solutions, and endpoint protection tools.
The Future of Application Control Engines
The world of cybersecurity is constantly evolving, and ACE technology is no exception. Here’s what the future may hold for ACEs:
1. Machine Learning and AI Integration
- Expect ACEs to increasingly adopt Machine Learning (ML) and Artificial Intelligence (AI). These technologies will enable ACEs to learn application behavior patterns, detect anomalies, and proactively block emerging threats.
2. Cloud-Based Deployment
- As businesses continue to embrace cloud computing, cloud-based ACE solutions will become more prevalent. These solutions are scalable, easier to manage, and accessible from anywhere, making them ideal for modern IT environments.
3. Zero Trust Architecture
- ACEs will play a crucial role in Zero Trust security models, enforcing strict access controls and continuous verification to ensure that users and devices can only access resources they are authorized to use.
4. Enhanced User Experience
- The user interface of ACEs will become more user-friendly, allowing IT teams to more easily develop and manage policies, streamlining deployment and management.
5. User Behavior Analytics (UEBA)
- ACEs may be integrated with UEBA solutions to track and analyze user behavior, enhancing the detection of insider threats and ensuring that only authorized users access sensitive applications.
Choosing the Right ACE for Your Business
There’s no one-size-fits-all when it comes to choosing an ACE. The best solution for your business will depend on several factors:
- Business Size and Industry: Larger businesses or those in regulated industries may require more sophisticated ACEs.
- Budget: While ACE solutions can be an investment, consider the long-term security benefits they provide.
- Security Requirements: Tailor the selection to your specific security needs, such as data protection, compliance, and malware prevention.
Steps to Choose the Right ACE:
- Understand Your Security Needs: Identify your business’s key security goals and vulnerabilities.
- Research ACE Vendors: Compare features, pricing, and customer reviews of different ACE solutions.
- Evaluate Scalability and Integration: Choose a solution that can grow with your business and integrate with your existing security tools.
Cisco ACE Application Control Engine: A Case Study
One of the leading solutions in the market is the Cisco ACE Application Control Engine. This advanced module is designed to enhance the availability, performance, and security of data center applications.
Key Features of Cisco ACE:
- Increased Application Availability: Cisco ACE uses advanced application switching algorithms to ensure that applications are always accessible, even in high-traffic conditions.
- Improved Performance: It accelerates application delivery, reducing latency and enhancing overall user experience.
- Enhanced Security: Cisco ACE performs deep packet inspection, blocking malicious traffic and providing robust security for applications and servers.
- High Scalability: The Cisco ACE module offers throughput of up to 16 Gbps per module, with the option to scale by adding up to four modules in a single chassis. This scalability is ideal for growing businesses and expanding data centers.
- Virtualization: Cisco ACE supports virtualization, allowing multiple applications to be provisioned and managed efficiently within a single module, reducing hardware requirements and operational costs.
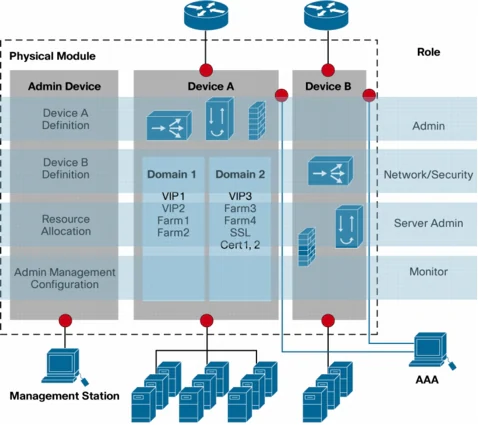
- Role-Based Administration: Cisco ACE enables role-based access control, streamlining the management of security policies and improving overall operational efficiency.
Source OF Information http://www.cisco.com/go/ace credit to : Cisco
Figure 1. Cisco ACE Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers

Figure 2. Cisco ACE Network Integration
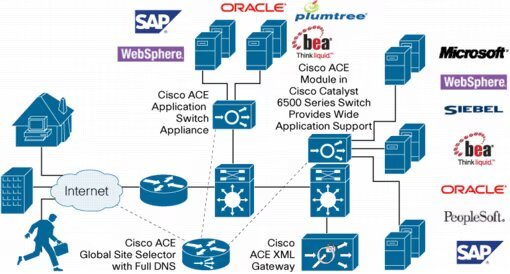
Figure 3. Cisco ACE Virtual Devices and Role-Based Administration
For More Information
For more information about the Cisco ACE, visit http://www.cisco.com/go/ace or contact your local Cisco account representative.
Conclusion
An Application Control Engine (ACE) is an essential security tool in today’s digital landscape. By controlling and monitoring application activity, ACEs prevent unauthorized access, malware infections, and data breaches. As the cybersecurity landscape continues to evolve, ACEs will become even more advanced, incorporating artificial intelligence, machine learning, and integration with cloud services to provide robust protection. Choosing the right ACE depends on your business’s size, industry, and specific security needs, so it’s essential to do thorough research before making a decision. Whether you’re looking for basic protection or a comprehensive solution, ACEs like Cisco ACE can help safeguard your business and streamline your IT operations.